What is a Transparent Proxy? In the ever-evolving landscape of Internet communication and cybersecurity, transparent proxy servers have emerged as an essential component of network infrastructure. Acting as intermediaries between users and web servers, transparent proxy servers play a pivotal role in enhancing security, optimizing performance, and enabling network monitoring.
Understanding the concept and functionality of transparent proxy servers is crucial for individuals and organizations seeking to safeguard their digital interactions, improve browsing speeds, and maintain a proactive stance against potential threats. In this article, we delve into the depths of transparent proxy servers, exploring their definition, working mechanism, advantages, disadvantages, and various use cases across different platforms.
Understanding Transparent Proxy Servers
Before diving into the specifics of transparent proxy servers, let’s have a recap on what a proxy is. In the realm of computer networks, a proxy acts as an intermediary between a client and a destination server. When a user makes a request to access a resource, such as a website or a file, the request is first sent to the proxy server. The proxy then forwards the request on behalf of the client to the destination server, retrieves the response, and relays it back to the client. In this process, the proxy server acts as a middleman, effectively hiding the client’s identity and protecting their privacy. For more information read What is a proxy article.

Different proxy types serve multiple purposes, including security enhancement, content filtering, and performance optimization. By acting as an additional layer between clients and servers, proxies can implement various protocols and mechanisms to improve network functionality and protect against potential threats. Different types of proxies exist, each catering to specific needs and offering distinct functionalities. One such type is the transparent proxy server, which we will delve into in the subsequent sections.
How Does a Transparent Proxy Work?
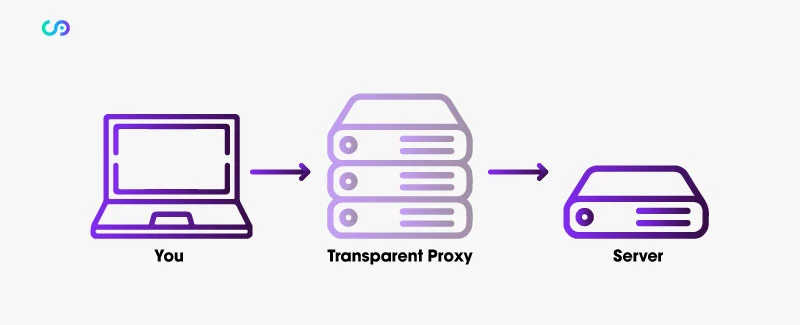
A transparent proxy server operates in a way that is transparent to both the client and the destination server. Unlike other types of proxies that may require client-side configurations or explicit routing, transparent proxies function without the need for any client-side modifications. This transparency aspect makes them seamless and inconspicuous in the network architecture.
When a client sends a request, it is unaware that it is being intercepted and forwarded by a transparent proxy. The transparent proxy server sits between the client and the destination server, silently intercepting all outgoing requests from the client. It then evaluates the request, applies any necessary filters or modifications, and forwards it to the destination server on behalf of the client.
From the perspective of the destination server, the transparent proxy appears as the originator of the request, hiding the client’s identity and IP address. This allows for increased anonymity and privacy for the client, as their direct connection to the destination server remains undisclosed.
It’s worth noting that the term “transparent” refers to the transparency of the proxy’s operation, rather than its visibility or disclosure to the user. In most cases, users are unaware of the presence of transparent proxies within their network infrastructure, as the proxies seamlessly intercept and forward requests without any noticeable impact on the browsing experience.
Transparent Proxy vs Regular Proxy
To better understand the role of transparent proxy servers, it’s essential to differentiate them from regular proxies. While both types of proxies serve as intermediaries between clients and servers, there are notable distinctions in their functionality and deployment.
Regular proxies, also known as forward proxies or explicit proxies, require explicit client-side configuration. Users must configure their web browsers or network settings to route their traffic through the proxy server explicitly. Regular proxies are commonly used in scenarios where users have control over their network settings and can manually specify the proxy server’s address and port.
On the other hand, transparent proxy servers do not require any client-side configuration. They operate at the network level, intercepting traffic without the need for explicit client involvement. Transparent proxies are typically deployed at the network gateway or router level, allowing them to intercept all outgoing traffic from the client devices within the network.
The key distinction lies in the level of transparency and user awareness. While regular proxies require client configuration and are visible to users, transparent proxies function behind the scenes, transparently intercepting and forwarding traffic without the user’s knowledge.
It’s important to note that the choice between a regular proxy and a transparent proxy depends on the specific use case and requirements. Regular proxies provide more control and flexibility for users to specify proxy settings, while transparent proxies offer a seamless and transparent operation without requiring any manual configuration.
Transparent Proxy Pros and Cons
Transparent proxy servers offer several advantages in terms of security, performance, and network management:
Enhanced Security: Transparent proxies can serve as an additional layer of defense against malicious content and potential threats. They can inspect incoming and outgoing traffic, filter out harmful or suspicious elements, and block access to malicious websites. By intercepting and analyzing network traffic, transparent proxies help mitigate the risk of malware infections, phishing attacks, and other security breaches.
Improved Performance: Transparent proxies can optimize network performance by caching frequently accessed content. When a client requests a resource, the proxy server checks its cache first. If the requested content is present in the cache, the proxy can serve it directly to the client without fetching it from the destination server. This caching mechanism reduces bandwidth usage, minimizes latency, and improves overall browsing speeds, particularly for repeated requests or popular content.
Bandwidth Optimization: Transparent proxies can effectively manage bandwidth usage by implementing policies such as content filtering and access control. They can prioritize critical network traffic, restrict access to bandwidth-intensive websites or protocols, and enforce fair usage policies. By regulating and optimizing bandwidth utilization, transparent proxies ensure a smoother network experience and prevent network congestion.
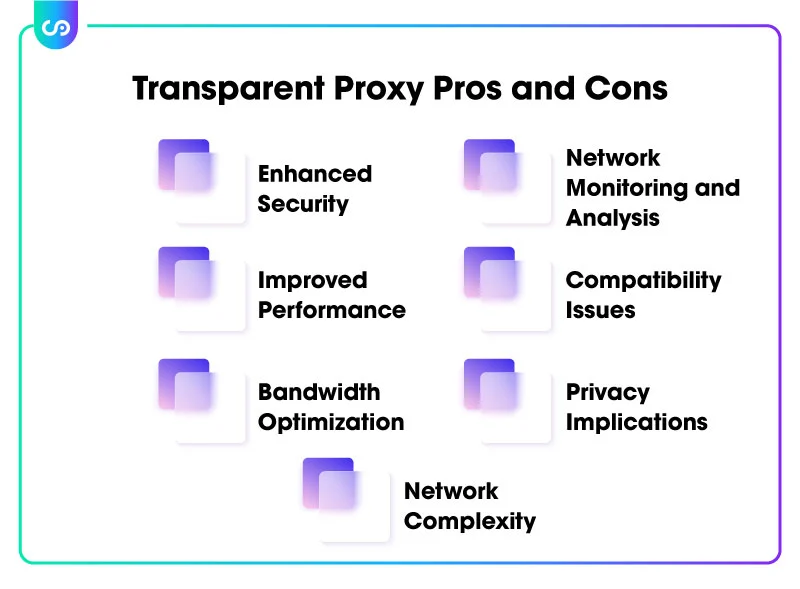
Network Monitoring and Analysis: Transparent proxy servers enable network administrators to monitor and analyze network traffic comprehensively. They can log and track incoming and outgoing connections, providing valuable insights into user activities, resource usage, and potential anomalies. This monitoring capability helps identify network issues, diagnose performance bottlenecks, and enforce acceptable use policies within the network.
While transparent proxy servers offer numerous benefits, it is important to consider potential disadvantages:
Compatibility Issues: Transparent proxies may encounter compatibility challenges with certain applications or protocols, particularly those that rely on specific network configurations or encryption. For example, some secure protocols, such as SSL/TLS, may pose challenges when transparent proxies attempt to intercept and inspect encrypted traffic. In such cases, additional configurations or techniques may be required to ensure compatibility.
Privacy Implications: The transparent nature of these proxies raises privacy concerns, as users may be unaware that their traffic is being intercepted and analyzed. While transparent proxies can enhance security, they also have the potential to collect and log user data, raising privacy implications. It is important to implement transparent proxies in a transparent and responsible manner, ensuring proper disclosure and adherence to privacy regulations.
Network Complexity: Implementing and managing transparent proxy servers can introduce additional complexity to the network infrastructure. It requires proper configuration, maintenance, and monitoring to ensure seamless operation and compatibility with other network components. Network administrators should have the necessary expertise and resources to deploy and manage transparent proxies effectively.
Despite these challenges, transparent proxy servers remain a valuable tool for organizations seeking to enhance security, optimize performance, and manage network resources effectively. By weighing the advantages and disadvantages, network administrators can make informed decisions regarding the implementation and utilization of transparent proxy servers within their infrastructure.
Transparent Proxy Modes and Configurations
In the world of proxy servers, different modes of operation exist to cater to various network requirements. One such mode is the transparent proxy mode, which offers unique advantages and capabilities. Transparent proxy mode stands out for its ability to intercept and process network requests seamlessly without requiring any configuration changes on the client side. Let’s delve deeper into understanding this mode and its significance.
When a transparent proxy server is deployed, it operates transparently between the client and the destination server, acting as an intermediary without the client’s knowledge. Unlike other proxy modes, such as explicit proxy mode where clients must explicitly configure their network settings, transparent proxy mode requires no additional configuration on the client’s end. This transparent nature makes it an attractive option for network administrators and IT professionals.
One of the key advantages of transparent proxy mode is its ability to seamlessly intercept and redirect network traffic. When a client sends a request to a destination server, the transparent proxy server intercepts the request in the background and forwards it on behalf of the client. This interception process occurs transparently, without any disruption to the client’s experience. From the client’s perspective, it appears as if the request is directly reaching the destination server.
Additionally, transparent proxy mode maintains invisibility and transparency by ensuring that the original source IP address of the client remains unchanged. This means that the destination server sees the request coming from the transparent proxy server, rather than the client’s device. This can be advantageous in scenarios where anonymity or hiding the client’s IP address is desired.
Transparent Proxy in Linux
Linux, being a popular and versatile operating system, provides robust support for transparent proxy servers. Configuring a transparent proxy server in a Linux environment can be accomplished using various tools and frameworks. Here are a few insights into implementing transparent proxy servers in Linux:
- IPTables: IPTables is a powerful firewall utility in Linux that can be used to redirect network traffic to a transparent proxy server. By manipulating IPTables rules, you can redirect specific traffic flows to the transparent proxy, allowing it to intercept and process the requests seamlessly.
- Squid Proxy: Squid is a widely-used proxy server software that supports transparent proxying. With Squid, you can configure transparent proxy mode by modifying its configuration file to intercept and forward network requests transparently. Squid also offers additional features like caching and access control, making it a versatile choice for transparent proxy deployment.
- HAProxy: HAProxy is another popular tool used for load balancing and proxying in Linux environments. It can also be configured to operate in transparent proxy mode by leveraging its powerful configuration options. HAProxy offers robust load balancing capabilities alongside transparent proxy functionality, making it suitable for high-traffic scenarios.
When configuring transparent proxy servers in Linux, it is crucial to ensure that the necessary network routing and firewall rules are properly set up. Additionally, SSL/TLS interception, a common requirement for transparent proxies, may require additional configurations and certificates to ensure secure communication between the client, transparent proxy, and the destination server.
By leveraging the flexibility and power of Linux, administrators and IT professionals can implement transparent proxy servers tailored to their specific needs. Linux’s extensive community support and wide array of tools make it an ideal platform for deploying transparent proxy solutions that enhance network security, performance, and monitoring capabilities.
Transparent Proxy Server Use Cases
Security Enhancement: In an era where cyber threats continue to evolve and pose significant risks to organizations and individuals alike, transparent proxy servers offer a valuable line of defense for enhancing network security. Let’s explore how transparent proxies play a crucial role in fortifying security measures.
One of the primary benefits of transparent proxy servers in terms of security enhancement is their ability to inspect and filter network traffic in real-time. Transparent proxies act as gatekeepers, analyzing each incoming and outgoing request, and determining whether it complies with predefined security policies. This allows for the detection and prevention of malicious activities such as malware infections, phishing attempts, and data exfiltration.
By inspecting the content of network traffic, transparent proxy servers can identify and block suspicious or unauthorized communication. They can scan web pages, emails, and file downloads for known malware signatures, helping prevent infections before they reach end-user devices. Additionally, transparent proxies can leverage advanced security technologies, such as intrusion detection and prevention systems (IDPS), to detect and thwart sophisticated attacks.
Transparent proxies also play a crucial role in enforcing web filtering and access control policies. Organizations can leverage transparent proxy servers to block access to malicious websites, inappropriate content, or websites that violate acceptable usage policies. This ensures that employees or network users are protected from potential threats, while also promoting productivity and compliance within the network environment.
Moreover, transparent proxies provide the ability to log and analyze network traffic in detail. By capturing and storing information about incoming and outgoing connections, transparent proxy servers offer valuable insights into potential security incidents or suspicious patterns. Security teams can review these logs to identify anomalies, investigate security breaches, and take proactive measures to strengthen their overall security posture.

Network Monitoring: Network monitoring is essential for maintaining a healthy and optimized network infrastructure. Transparent proxy servers offer powerful capabilities for monitoring and analyzing network traffic, enabling administrators to gain valuable insights and troubleshoot issues effectively.
Transparent proxy servers act as intermediaries between clients and destination servers, allowing them to log and monitor all network requests and responses passing through them. This means that administrators can gain detailed visibility into the types of websites visited, the applications being used, and the volume of data transferred. This information can be invaluable for capacity planning, identifying bottlenecks, and optimizing network performance.
With transparent proxy servers, administrators can also implement bandwidth management strategies more effectively. By analyzing the bandwidth usage patterns, they can identify applications or users that consume excessive bandwidth, prioritize critical traffic, and enforce fair usage policies. This not only optimizes network performance but also helps avoid bandwidth congestion and ensures a smooth user experience.
Additionally, transparent proxy servers enable administrators to monitor user activity and enforce compliance with acceptable usage policies. By reviewing logs and analyzing network traffic, administrators can identify unauthorized access attempts, detect insider threats, and enforce compliance with regulations such as data protection and intellectual property rights.
Transparent proxy servers also provide a platform for advanced network analysis. By capturing and storing network traffic data, administrators can leverage specialized tools and techniques to perform deep packet inspection, protocol analysis, and performance monitoring. This allows for the identification of abnormal network behavior, troubleshooting network issues, and ensuring the overall health and integrity of the network infrastructure.
In summary, transparent proxy servers offer significant advantages in terms of security enhancement and network monitoring. By inspecting and filtering network traffic, transparent proxies help prevent malware infections, phishing attempts, and enforce web filtering policies. They also provide comprehensive visibility into network activity, facilitating effective network monitoring, troubleshooting, and performance optimization. Deploying transparent proxy servers can greatly enhance an organization’s security posture and contribute to a more resilient and efficient network environment.
Transparent Caching Proxy
In today’s fast-paced digital world, where internet content is accessed and shared at a rapid rate, transparent caching proxy servers offer an effective solution for improving network performance and reducing bandwidth consumption. Let’s explore the concept of transparent caching proxies and their benefits.
A transparent caching proxy server works by storing frequently accessed web content locally, allowing subsequent requests for the same content to be served directly from the cache rather than fetching it from the original source server. This caching mechanism brings several advantages to the table.
One of the primary benefits of transparent caching proxies is the significant improvement in content delivery speed. By serving cached content locally, transparent caching proxies reduce the latency associated with retrieving data from remote servers. This leads to faster loading times for websites, images, videos, and other web-based resources. Users experience a noticeable boost in browsing speed and overall responsiveness, enhancing their browsing experience.

Transparent caching proxies also help alleviate network congestion and reduce bandwidth consumption. When multiple users within a network request the same content, the caching proxy only needs to retrieve it from the original server once. Subsequent requests for the same content are served directly from the cache. This saves valuable bandwidth and reduces the load on the network infrastructure, leading to more efficient utilization of available resources.
Additionally, transparent caching proxies can optimize network performance by reducing the amount of data transferred between the client and the server. Caching commonly accessed content eliminates the need to download the same data repeatedly, resulting in lower data transfer volumes. This is particularly beneficial for organizations with limited bandwidth or remote locations where internet connectivity is less robust.
Furthermore, transparent caching proxies can enhance the availability and resilience of web content. In cases where the original source server becomes temporarily unavailable or experiences high traffic, the caching proxy can continue to serve cached content, ensuring uninterrupted access to critical resources. This feature is particularly advantageous for websites or applications that experience sudden surges in traffic or intermittent connectivity issues.
Leveraging Transparent Caching Proxies for Performance Optimization
To fully harness the benefits of transparent caching proxies, organizations can implement specific strategies and configurations to optimize their caching infrastructure:
- Cache-Control Headers: Websites and web applications can include Cache-Control headers in their responses to instruct caching proxies on how long the content should be stored in the cache. By appropriately setting these headers, organizations can balance freshness and efficiency, ensuring that frequently changing content is updated while reducing unnecessary cache invalidations.
- Content Filtering: Transparent caching proxies can be configured to filter specific content from being cached. This is useful for dynamic content or content that should not be cached due to privacy concerns or security considerations. By selectively caching appropriate content, organizations can strike a balance between performance improvement and content integrity.
- Cache Sizing and Replacement Policies: Transparent caching proxies offer options for adjusting cache sizes and defining replacement policies. Organizations can allocate sufficient storage space for caching and configure policies that prioritize frequently accessed or time-sensitive content, ensuring optimal cache utilization and maintaining the freshness of critical resources.
- Content Pre-warming: To ensure that popular content is readily available in the cache, organizations can implement pre-warming techniques. This involves proactively fetching and caching frequently accessed content during periods of low network traffic, ensuring that users can immediately benefit from the performance boost provided by the transparent caching proxy.
By implementing these strategies and fine-tuning the configuration of transparent caching proxies, organizations can significantly enhance the performance and efficiency of their network infrastructure. Users will enjoy faster browsing speeds, reduced latency, and improved overall responsiveness while making more efficient use of available bandwidth.
In conclusion, transparent caching proxy servers offer substantial benefits for organizations aiming to optimize network performance and reduce bandwidth consumption. By caching frequently accessed content locally, transparent caching proxies improve content delivery speed, alleviate network congestion, and enhance the availability of web resources. Implementing appropriate caching strategies empowers organizations to maximize the advantages of transparent caching proxies, providing users with a seamless and efficient browsing experience.
Transparent Proxy Logging and Monitoring
Transparent proxy logging and monitoring are essential components for maintaining network security, analyzing network traffic, and detecting potential issues. By capturing and analyzing relevant data, organizations can gain valuable insights into network behavior and take proactive measures to ensure a secure and optimized network environment.
Transparent proxy logging involves recording detailed information about network requests and responses passing through the proxy server. This includes data such as source and destination IP addresses, timestamps, URLs, HTTP headers, and more. By logging this information, organizations can track user activity, identify potential security threats, and investigate network incidents or performance issues.

Monitoring transparent proxy logs allows administrators to analyze network traffic patterns, identify anomalies, and detect suspicious activities. By leveraging specialized monitoring tools and techniques, organizations can gain real-time visibility into network behavior, helping them make informed decisions and respond quickly to security events or network performance degradation.
Furthermore, transparent proxy logging and monitoring facilitate compliance with regulatory requirements and internal policies. By maintaining detailed logs of network activity, organizations can demonstrate adherence to data protection standards, monitor compliance with acceptable usage policies, and fulfill audit requirements.
Conclusion
Understanding what a transparent proxy is and how it functions is crucial for organizations seeking to enhance their network infrastructure. Transparent proxies serve as intermediaries, intercepting and forwarding network requests seamlessly without requiring client-side configuration. They provide a range of benefits, including improved security, optimized performance, and efficient content delivery through caching commonly accessed resources. By leveraging transparent proxy technology, businesses can bolster their network security, streamline data transmission, and gain valuable insights into network activity. Embracing the power of transparent proxies empowers organizations to create a robust and resilient network environment, ensuring a seamless user experience and efficient utilization of network resources.
FAQs
How does a transparent proxy work?
A transparent proxy operates by intercepting network traffic without requiring any client-side configuration, seamlessly forwarding requests and responses between clients and servers, and often implementing caching mechanisms for improved performance.
What is the difference between proxy and transparent proxy?
A proxy acts as an intermediary between clients and servers, routing network traffic through a separate server. A transparent proxy, on the other hand, performs the same intermediary role but operates without the need for explicit client-side configuration, making it transparent to end users.
What is the difference between transparent and non-transparent proxy?
A transparent proxy operates behind the scenes, intercepting and forwarding network traffic without explicit configuration on client devices, ensuring seamless integration with existing network infrastructure. A non-transparent proxy, also known as an explicit proxy, requires explicit client-side configuration, such as setting the proxy server address and port, to redirect traffic through the proxy.
What are the advantages of using a transparent proxy?
Using a transparent proxy offers several advantages, including improved security through real-time traffic inspection and filtering, enhanced performance by caching frequently accessed content, reduced bandwidth consumption by optimizing data transfer, and simplified network management with seamless integration into existing infrastructure.







